symmetric encryption
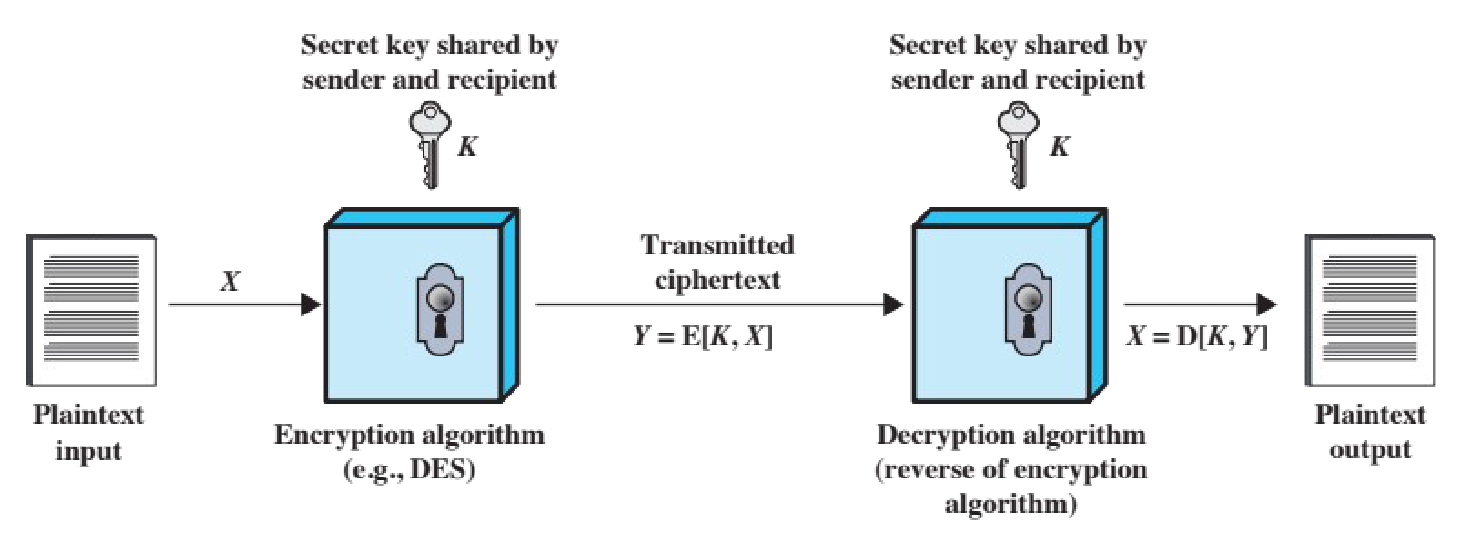
Symmetric encryption (or single-key encryption / conventional encryption) is the universal technique for providing confidentiality for transmitted or stored data.
It uses a single, shared key to both encrypt and decrypt data.
Two requirements need to be met for secure use:
- a strong encryption algorithm
- sender and receiver must have obtained copies of the secret key in a secure fashion, and must keep the key secure
simplified model
attacks
There are two kinds of attacks used on symmetric encryption:
- cryptoanalytic attacks ⟶ rely on the nature of the algorithm, knowledge of the general characteristics of the plaintext, or some plaintext-ciphertext pairs
- they exploit the characteristics of an algorithm to attempt to deduce a plaintext or a key (if successful, all future and past messages encrypted with that key are compromised)
- these types of attacks are mainly used to reduce the dictionary of a possible brute-force attacks, but they have become outdated due to the new standards of encryption
- brute-force attacks ⟶ all possible keys are tried until an intelligible translation into plaintext is obtained (on average, half of all possible keys must be tried)
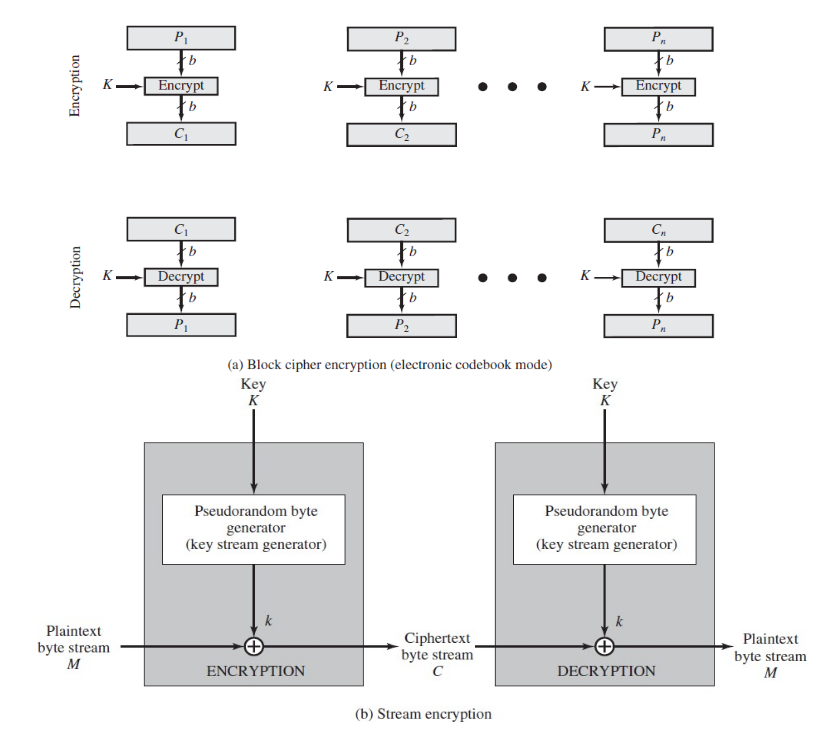
block vs stream cyphers
| block cyphers | stream cyphers |
|---|---|
| process the input one block of elements at a time | process input elements continuously (encrypt plaintext one byte at a time) |
| produce an output block for each input block | produce output one element at a time |
| can reuse keys | faster to use (+ less code) |
| more common | pseudorandom streams are unpredictable without knowledge of the input key |
most known symmetric encryption algorithms
- AES (Advanced Encryption Standard / Rijndael)
- 128-bit block cypher + 128 / 192 / 256-bit secret keys
- most popular and widely used
- DES (Data Encryption Standard) (or DEA, Data Encryption Algorithm)
- 64 plaintext block + 56 bit key = 64 bit cypher block
- now considered insecure due to the shortness of the key
- 3DES ⟶ repeats DES threee times using either two or three unique keys
- (168-bit key
- RC4 (ARC4)
- stream cipher with 40-2048-bit secret keys
- considered insecure
message authentication
Message authentication is used for protection against active attacks. Received messages are verified to be authentic: contents have not been altered, the source is authentic, and they arrived timely and in correct sequence.
- Message authentication can use conventional encryption (only sender and receiver share a key).
Message encryption by itself doesn’t provide a secure form of authentication. However, authentication and confidentiality can be combined in a single algorithm by using encryption + authentication tag.
- typically, though, message authentication is separate from message encryption, and it can be needed without the need for confidentiality (e.g. in broadcasts)
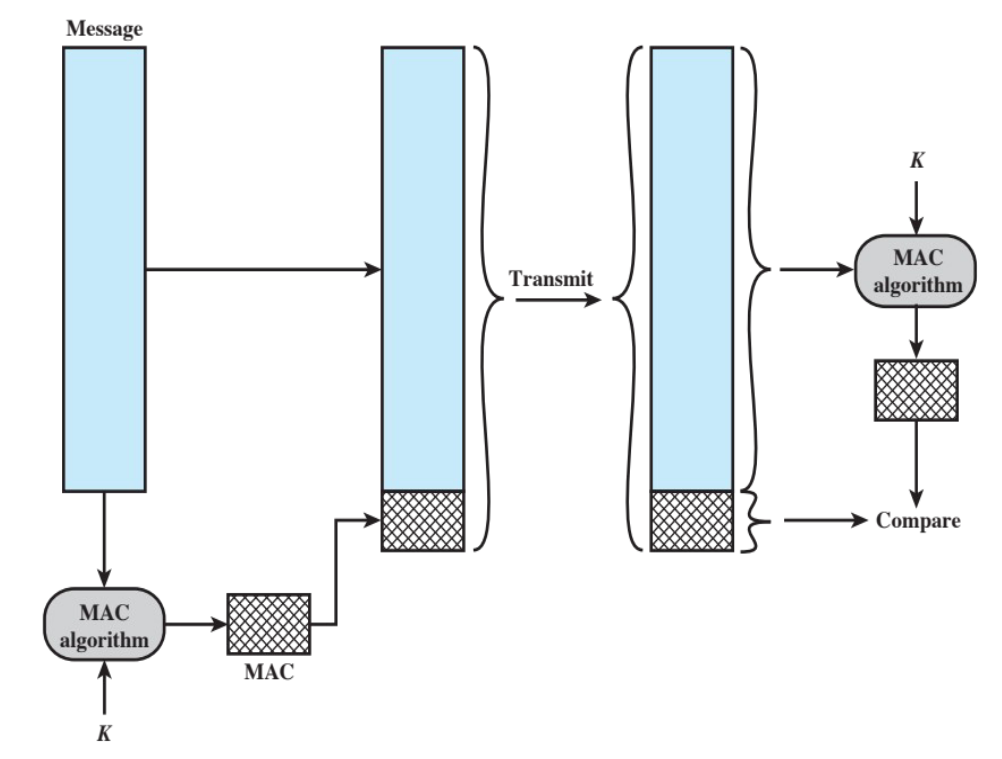
Message Authentication Code (MAC)
A Message Authentication Code is used to verify the integrity and authenticity of a message. It can be generated by many different algorithms, but it is required that the authentication algorithm need not be reversible.
MAC
- the MAC takes a secret key as input; the receiver compares the code it can generate with the key with the one it received
hash functions
cryptographic hash functions
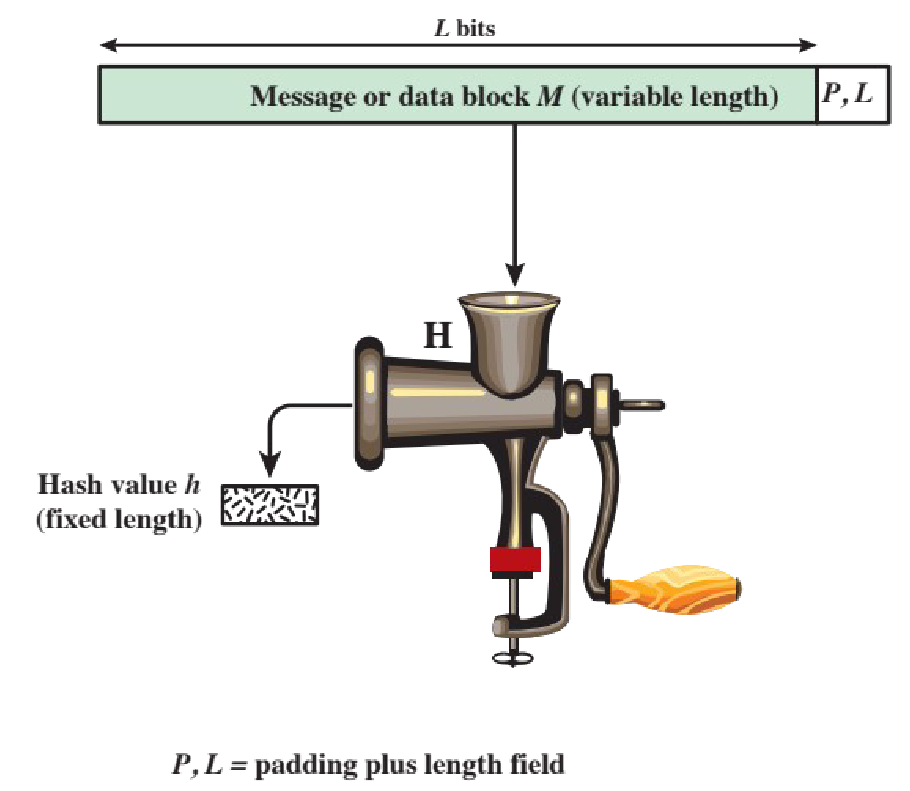
The purpose of a hash function is to produce a “fingerprint” for a block of data.
- it generates a set of
kbits from a set ofL>=kbits- it’s usually necessarily non-injective
- the result of applying a hash function is called hash value or cheksum or message digest
properties for a hash function aimed at authentication
- can be applied to a block of data of any size
- produces a fixed-length output
- is relatively easy to compute
- one-way or pre-image resistant - computationally infeasible given , to find s.t.
- computationally infeasible to find s.t.
- collision-resistant - computationally infeasible to find s.t.
There are two approaches to attacking a secure hash function:
- exploiting logical weaknesses in the algorithm
- the shorter the hash code produced by the algoritm, the weaker the function
The most-used hash algorithm is SHA.
additional secure hash function applications
- hash of a password is stored by an operating system
- , for each file , is stored on a system and the hash values are secured
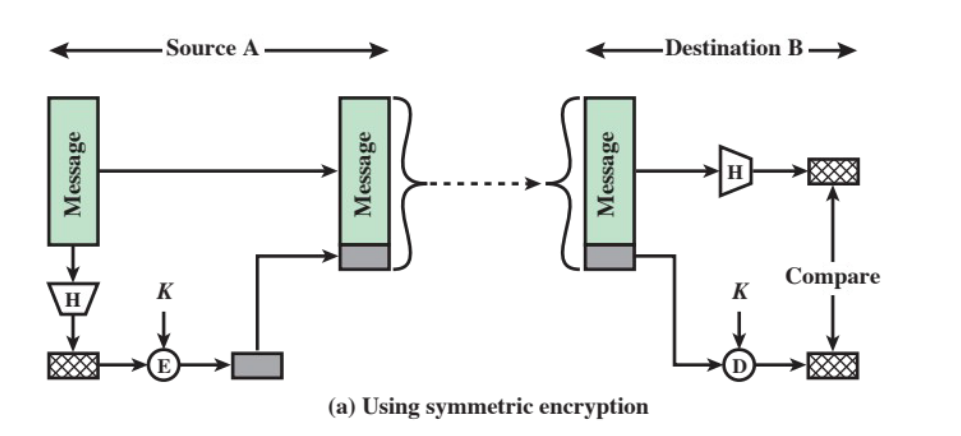
MAC with one-way hash functions
Unlike the MAC, hash functions don’t take secret keys as input. It is, however, possible to get MACs using hash functions.
There are three different ways of using MAC with one-way hash functions:
using symmetric encryption
- the hash value is encrypted with a secret key
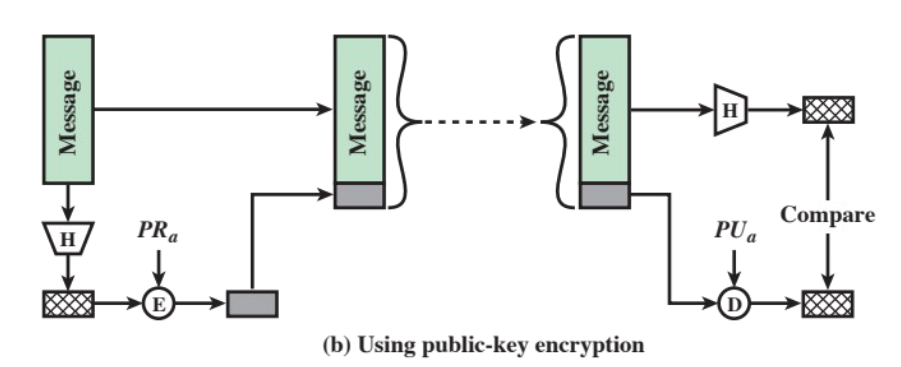
using public-key encryption
- the hash value is encrypted with the sender’s private key and decrypted with the receiver’s public key (more about public-key encryption below)
- this implementation provides a “digital signature”, as it proves the ciphertext came from a known sender (“identified” by its private key)
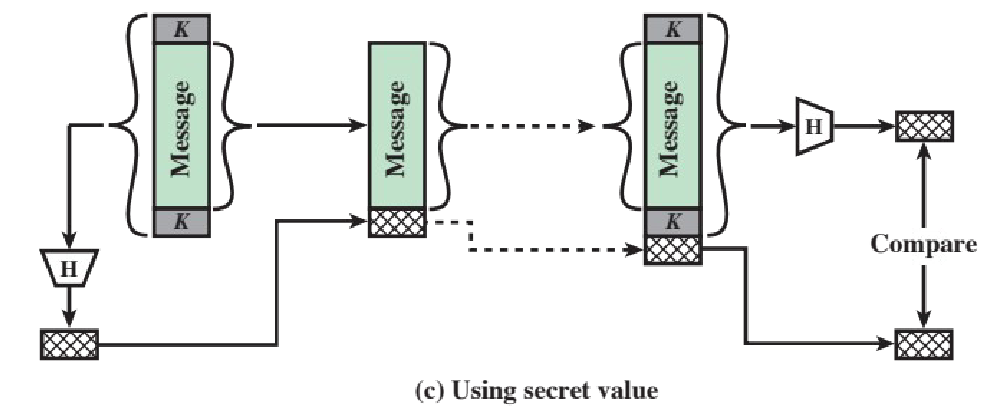
using secret value
- a secret key, known to both the sender and the receiver, is added at the start and end of the message that gets hashed
In all three implementations, authentication is ensured by the comparison between a new digest, generated by the receiver using the same hash function, and the hash it received.
public-key encryption
Public-key encryption is a form of asymmetric encryption (i.e. uses two separate keys: a public key, made public for anyone to use, and a private key,, known only to its owner) based on mathematical functions.
- a protocol is needed for distribution of the keys
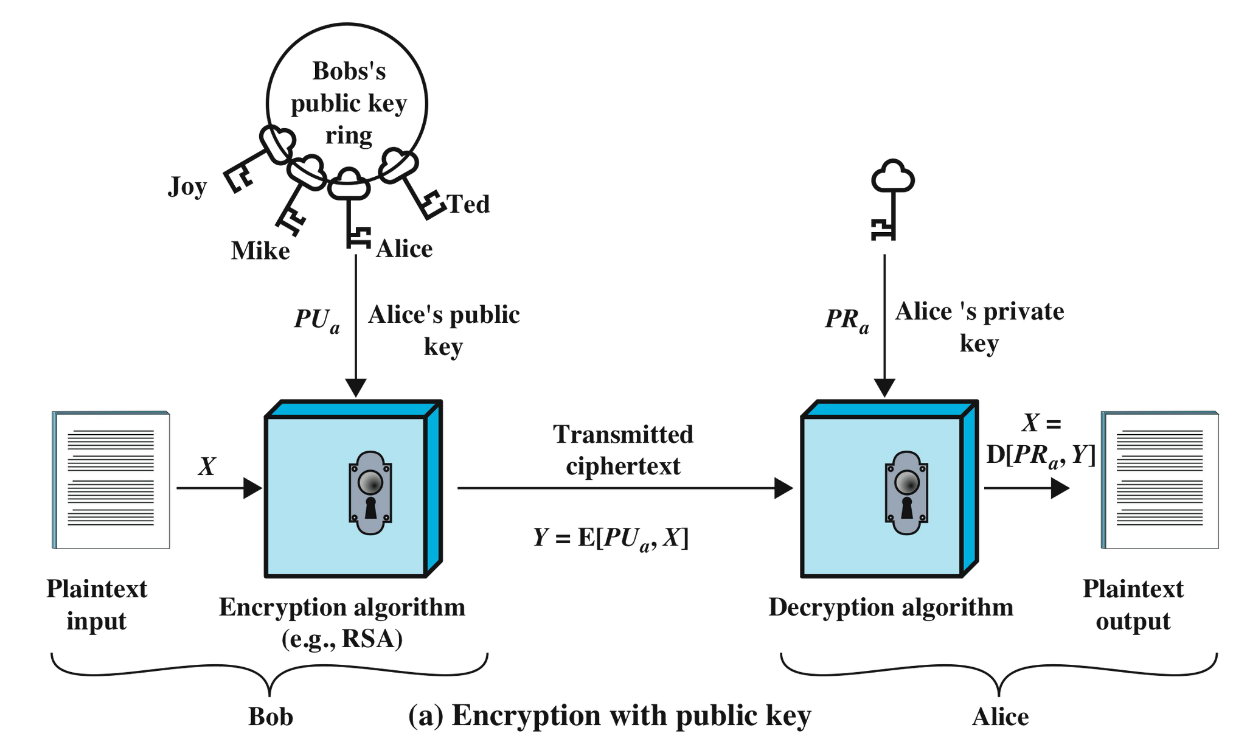
encryption with public key
decripting with a private key ensures confidentiality (only the receiver can decrypt)
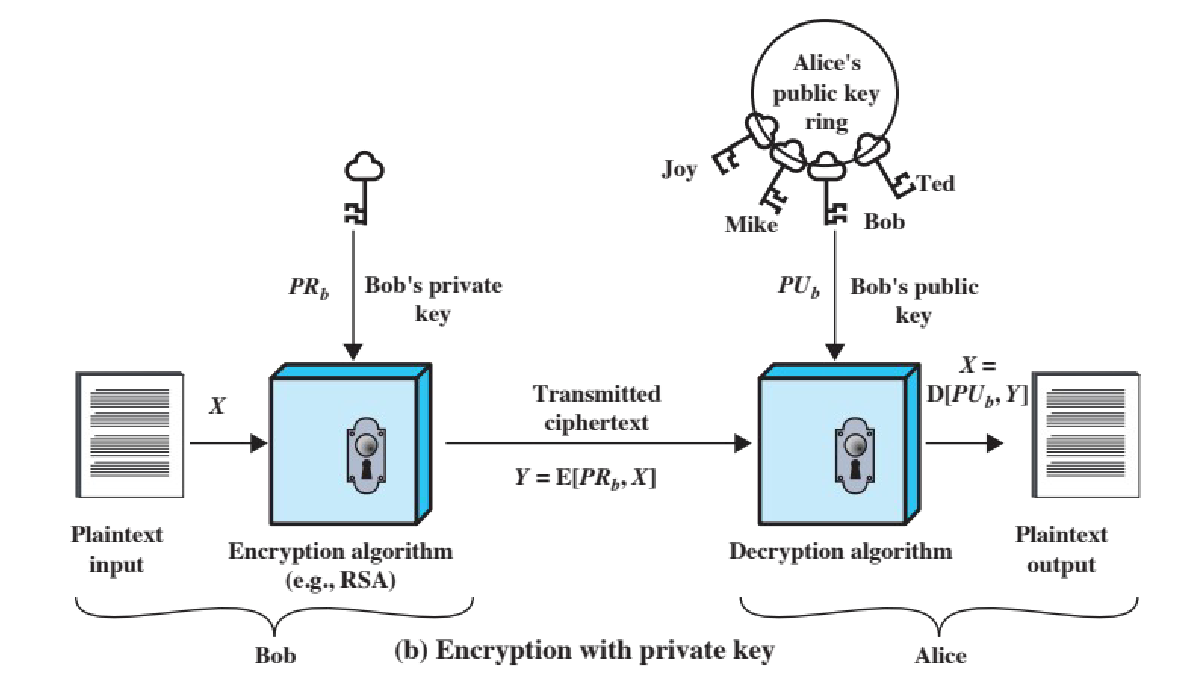
decryption with public key
encrypting with a private key ensures authenticity, but not confidentiality: anyone can decrypt with public keys
we can classify the use of public-key cryptosystems in three categories:
| algorithm | digital signature | symmetric key distribution | encryption of secret keys |
|---|---|---|---|
| RSA | yes | yes | yes |
| Diffie-Hellman | no | yes | no |
| DSS | yes | no | no |
| Elliptic Curve | yes | yes | yes |
these cryptosystems need to meet the following requirements:
- computationally easy to create key pairs
- computationally easy for sender knowing public key to encrypt messages
- computationally easy for receiver knowing private key to decrypt ciphertext
- computationally infeasible for opponent to determine private key from public key
- computationally infeasible for opponent to to otherwise recover original message
- useful if either key can be used for each role
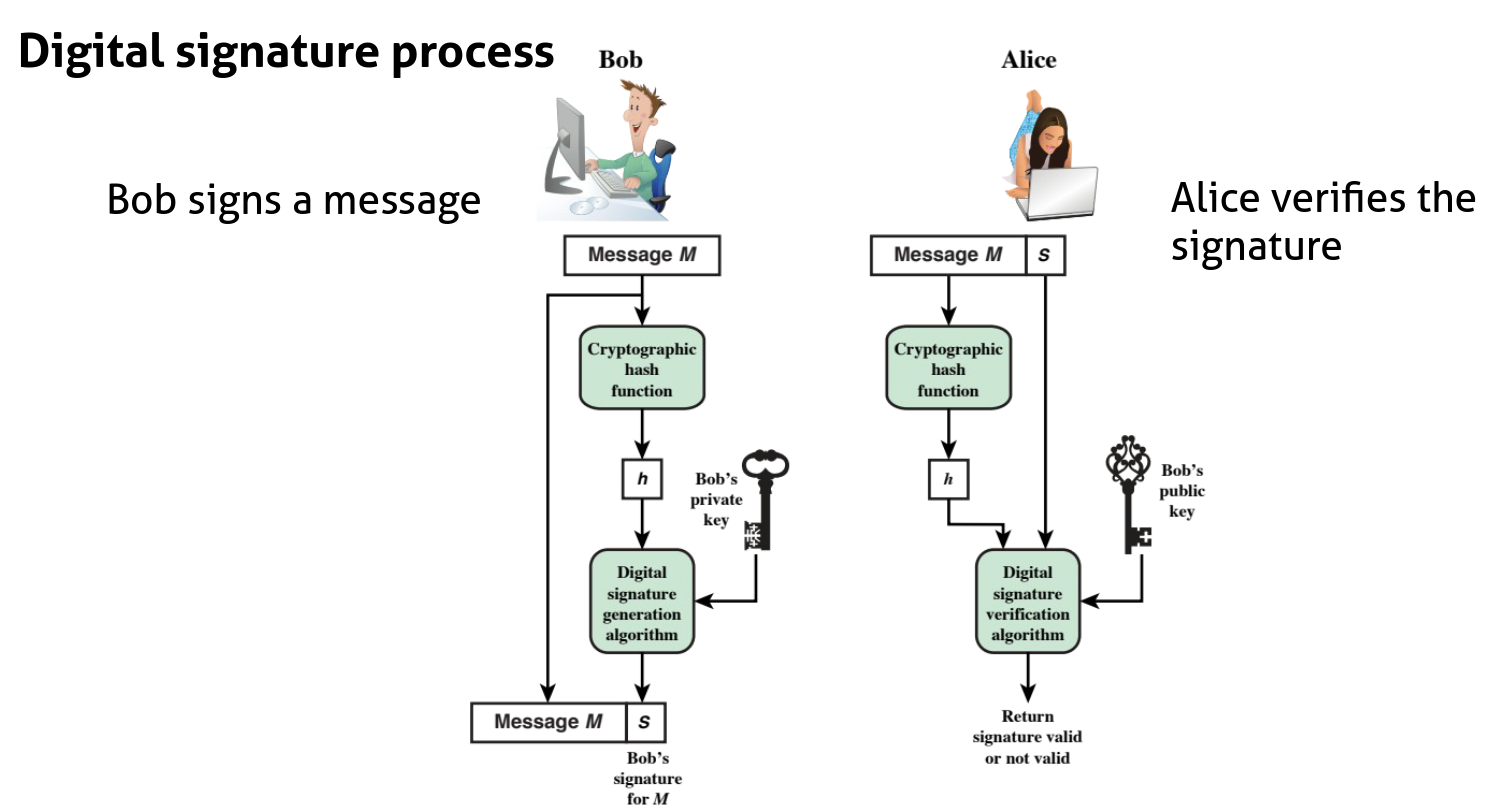
digital signature
definition by NIST
”The result of a cryptographic transformation of data that, when properly implemented, provides a mechanism for verifying origin authentication, data integrity and signatory non-repudiation.”
So, it’s a data-dependent bit pattern generated by an agent as a function of a data block.
process
public key certificate
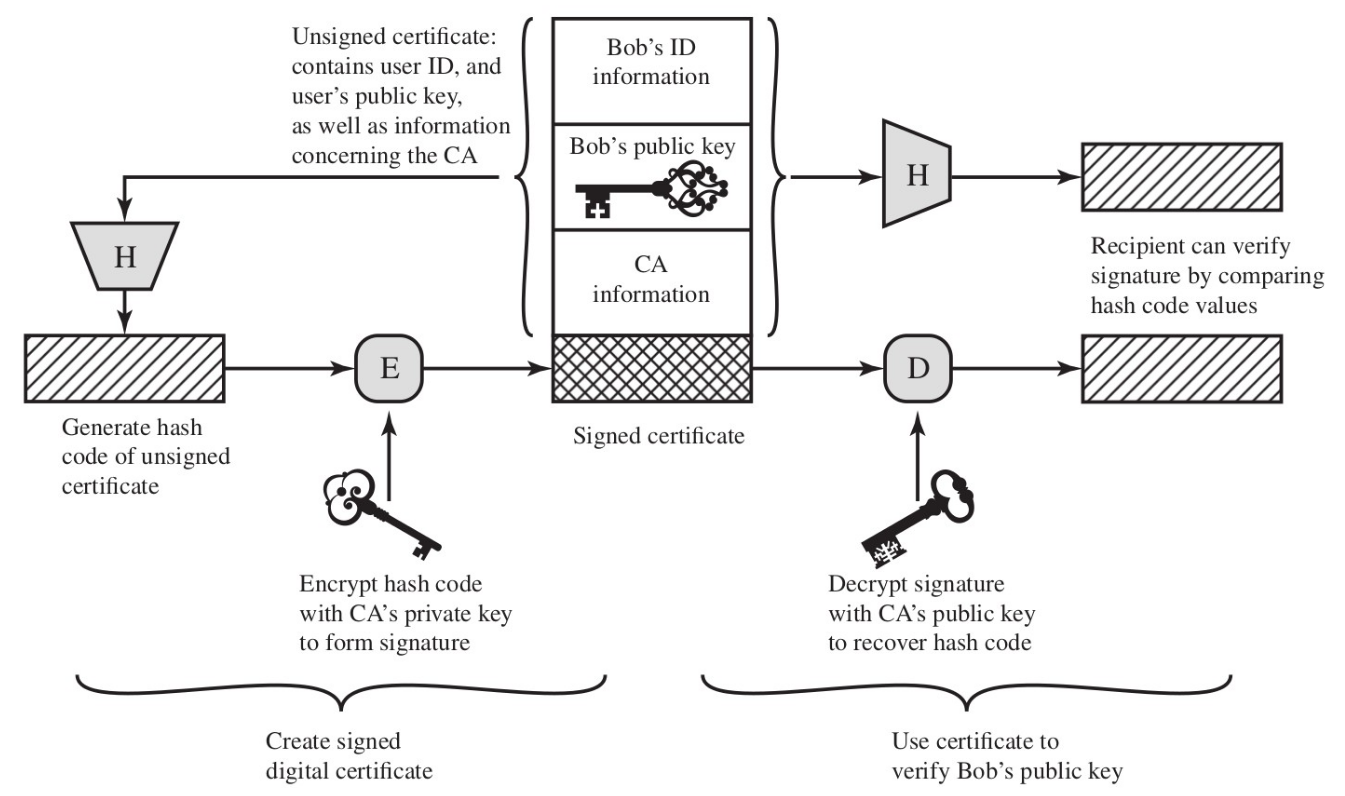
A public key certificate is an electronic document used to prove the validity of a public key. It includes the public key, information about it and about the identity of its owner, and the digital signature of an entity that has verified the certificate’s contents.
- in a public-key infrastructure scheme, the certificate issuer is often a certificate authority (CA), a company that charges customers to issue certificates for them
- by contrast, in a “web of trust” scheme, individuals sign each other’s keys directly
In case of key compromise, a certificate may need to be revoked.
digital envelope
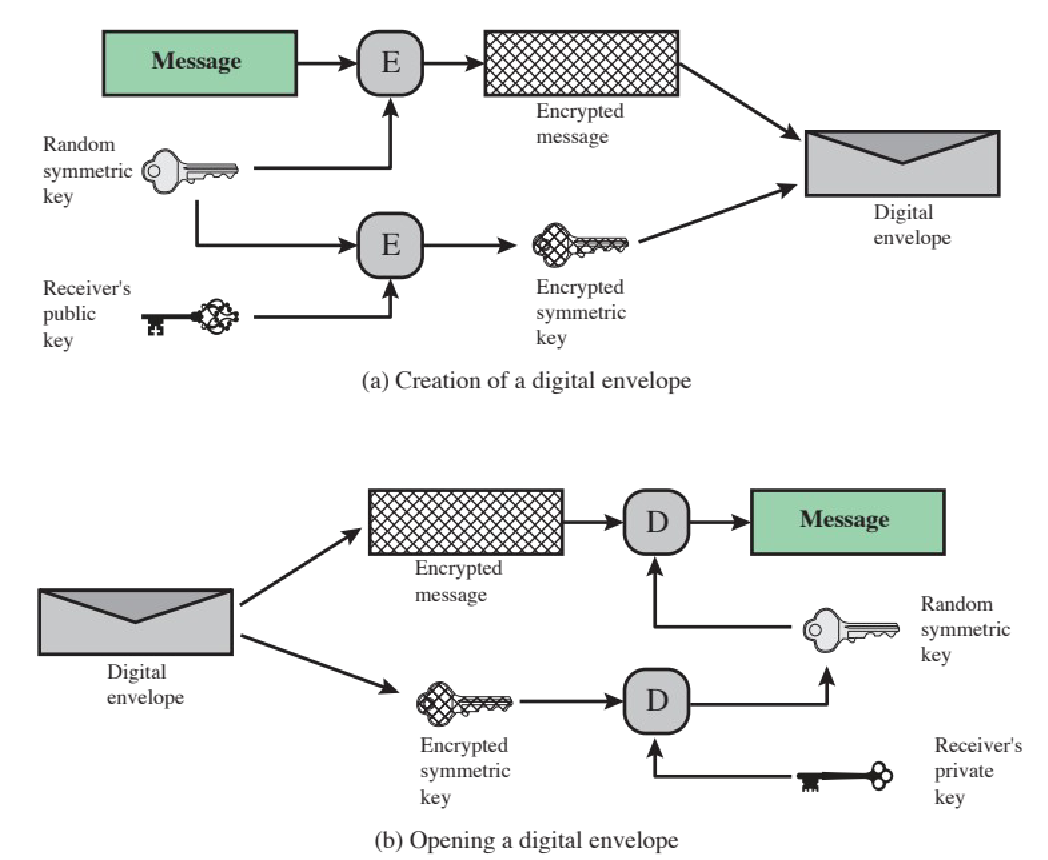
A digital envelope is a secure method for transmitting encrypted information using both symmetric and asymmetric encryption. The data is encrypted with a symmetric key, which is then encrypted with the recipient’s public key using asymmetric encryption (ensuring that only the intended recipient, who holds the corresponding private key, can decrypt the symmetric key and access the original data). The envelope contains both the data and the encrypted key - the receiver uses their private key to decrypt the encrypted key, then they use that for the message.
random numbers
Random numbers play an essential role in cybersecurity. Their uses include the generation of:
- keys for public-key algorithms
- stream keys for symmetric stream ciphers
- symmetric keys for use as a temporary sessione key, or in creating a digital envelope
- handshaking to prevent replay attacks
- session keys
Random numbers need to meet the following requirements:
- randomness and unpredictability
- uniform distribution ⟶ frequency of occurrency of each number should be approximately the same
- independence ⟶ no value in the sequence should be inferred from the others
random vs pseudorandom
cryptographic applications typically make use of algorithmic techniques for random number generation, but algorithms are deterministic and therefore produce sequences of numbers that are not statistically random (pseudorandom), and are likely to be predictable.
a TRNG (True Random Number Generator), by contrast, uses a nondeterministic source to produce randomness (like measuring unpredictable natural processes)
- fun example: Cloudflare uses lava lamps ! (https://www.cloudflare.com/learning/ssl/lava-lamp-encryption/)