cryptographic hash function
The purpose of a hash function is to produce a “fingerprint” of a file, message or block of data.
It generates a set of bits from a set of bits.
- a hash function is generally non-injective
The result of applying a hash function is called hash value, message digest or checksum.
MAC with one-way hash function
Unlike a MAC, a hash function doesn’t take a secret key as input - it is, however, possible to get MACs using hash functions.
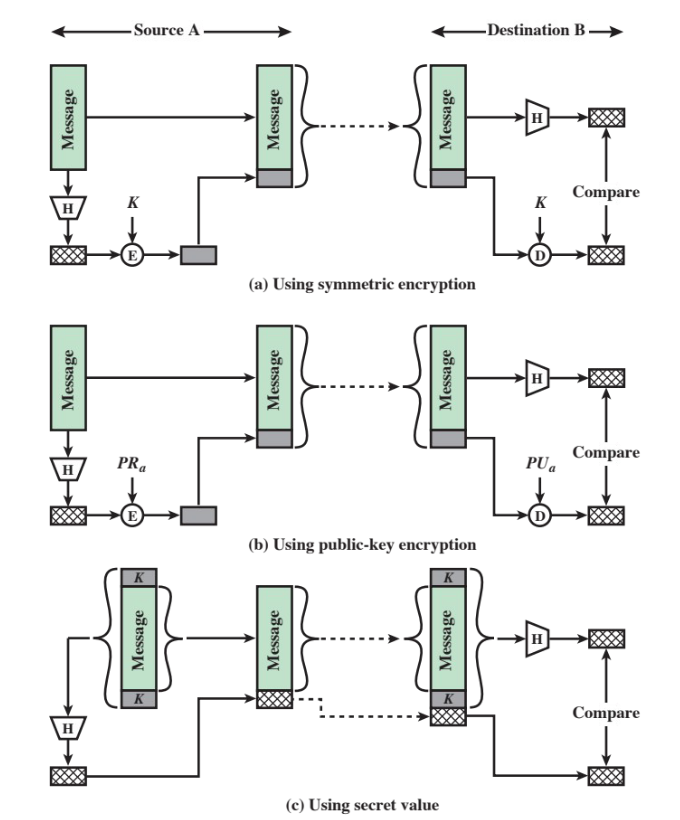
properties of a hash function aimed at authentication
- can be applied to a block of data of any size
- produces a fixed-length output
- is relatively easy to compute for any given
- computationally infeasible to find such that (one-way or pre-image resistant)
- computationally infeasible to find such that
- computationally infeasible to fiind such that (collision resistant)
There are two approaches to attacking a secure hash function:
- exploit logical weaknesses in the algorithm
- strength